Ghostwriter Strikes Back: New Phishing Campaign Targets Ukraine and Belarus

SentinelLABS has detected a new Ghostwriter campaign affecting opposition activists in Belarus and Ukrainian military and government entities. The campaign, which began in late 2024, uses weaponized Excel documents as phishing baits. The documents have obfuscated VBA macros that run malicious payloads when opened. The attack chain tends to start with a Google Drive link in the phishing email, which directs the victim to a RAR file containing the malicious Excel workbook. The timing of the campaign implies association with the January 26, 2025, Belarusian presidential election.
The Ghostwriter group, which is affiliated with the Belarusian state, employs sophisticated obfuscation mechanisms to avoid being detected. They alter their own memory layout and manipulate portable executable (PE) headers. The campaign incorporates fresh malware variants such as PicassoLoader and a newly created downloader. These attacks hold significant potential in terms of targeting individuals, allowing for data theft and long-term access to facilitate follow-on operations.
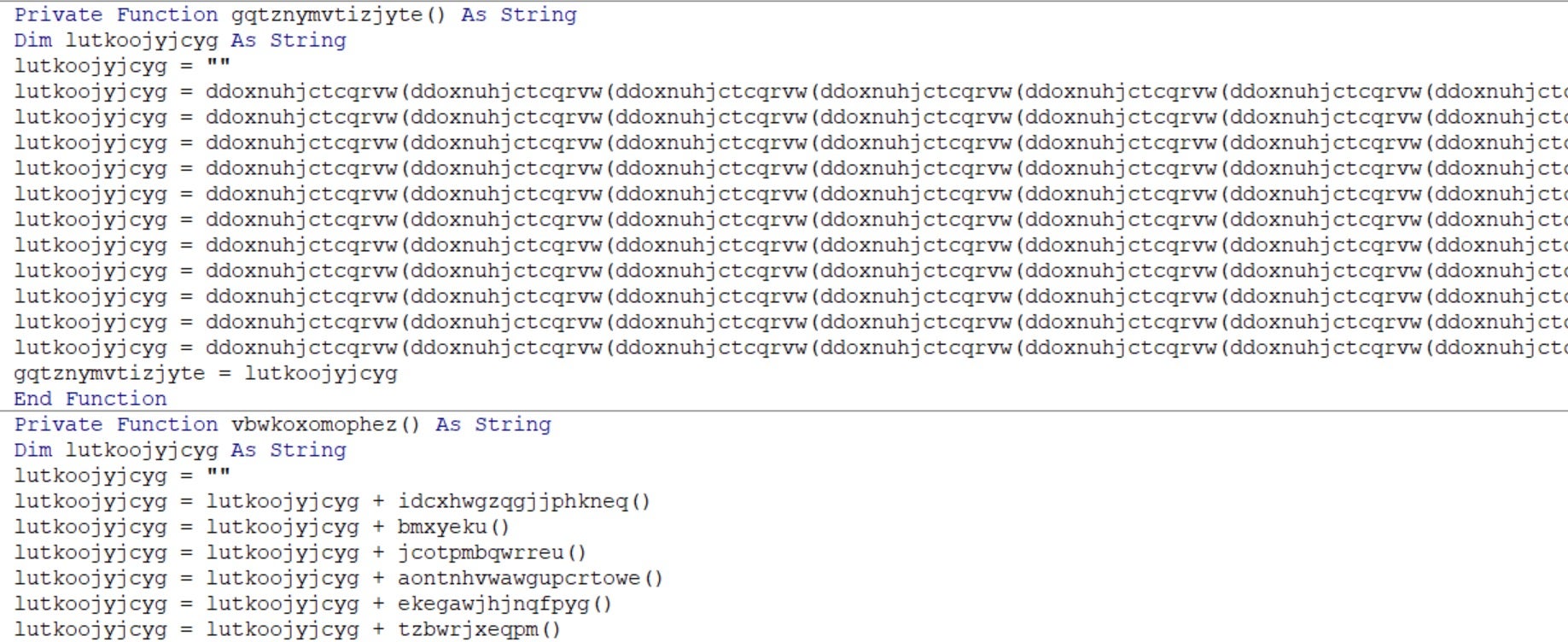
favorite techniques for threat hunting missions is the abuse of rundll32.exe. It's EXTREMELY common. Let's examine a recent Ghostwriter campaign described in a report by SentinelLABS.
In this campaign, the adversary actively abused rundll32.exe to execute malicious DLLs. Here are some procedure examples:
rundll32.exe "C:\Users<USER>\AppData\Roaming\Microsoft\bruhdll32.dll",FckUDud rundll32.exe "C:\Users<USER>\AppData\Roaming\Microsoft\bruhdll32.dll",HelloWorld rundll32.exe "C:\Users<USER>\AppData\Roaming\Microsoft\bruhdll32.dll",FCKU rundll32 "C:\Users<USER>\AppData\Roaming\Microsoft\SystemCertificates\CertificateCenter.dll",#1
The interesting function names are a good indication of suspicious activity. Additionally, each path includes "Roaming\Microsoft," which is worth noting.
Always pay attention to the paths used by threat actors to store malicious DLLs—it's great fuel for your rundll32.exe abuse hunting missions!
- Reference Link
favorite techniques for threat hunting missions is the abuse of rundll32.exe. It's EXTREMELY common. Let's examine a recent Ghostwriter campaign described in a report by SentinelLABS.
In this campaign, the adversary actively abused rundll32.exe to execute malicious DLLs. Here are some procedure examples:
rundll32.exe "C:\Users<USER>\AppData\Roaming\Microsoft\bruhdll32.dll",FckUDud rundll32.exe "C:\Users<USER>\AppData\Roaming\Microsoft\bruhdll32.dll",HelloWorld rundll32.exe "C:\Users<USER>\AppData\Roaming\Microsoft\bruhdll32.dll",FCKU rundll32 "C:\Users<USER>\AppData\Roaming\Microsoft\SystemCertificates\CertificateCenter.dll",#1
The interesting function names are a good indication of suspicious activity. Additionally, each path includes "Roaming\Microsoft," which is worth noting.
Always pay attention to the paths used by threat actors to store malicious DLLs—it's great fuel for your rundll32.exe abuse hunting missions!