New Phishing Kit Bypasses 2FA to Steal Credentials

A new and sophisticated phishing kit called Astaroth has emerged, posing a significant threat to email users and businesses by bypassing two-factor authentication (2FA). This toolkit is being used by cybercriminals to steal login credentials from Gmail, Yahoo, AOL, Office 365 (O365), and other platforms, making even accounts with additional security layers vulnerable.
How Astaroth Works
Astaroth employs session hijacking and real-time credential interception to bypass 2FA protections. According to cybersecurity researchers at SlashNext, who first discovered the campaign, the phishing kit uses advanced social engineering tactics to trick victims into entering their login credentials. Unlike traditional phishing attacks, which only steal usernames and passwords, Astaroth captures session tokens, enabling attackers to take over accounts **without needing to bypass additiona...
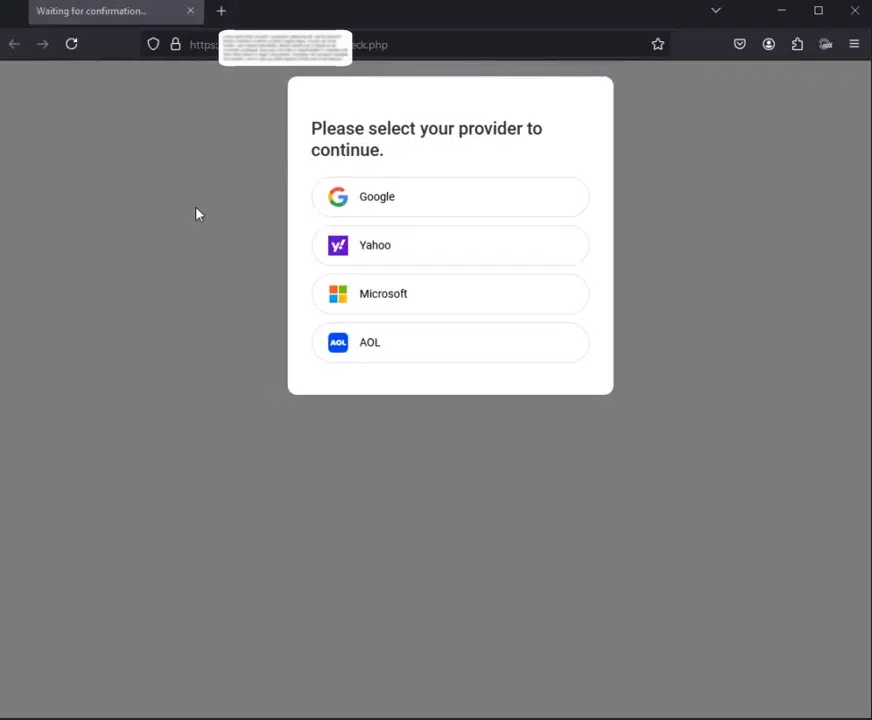
1. Victim’s View: A Fake Login Page
The attack begins when a victim is tricked into clicking a phishing link, often disguised as a legitimate login prompt for popular email services. As seen in the first screenshot, users are asked to select their provider (Google, Yahoo, Microsoft, or AOL), leading them to a convincing but fake login page designed to steal credentials.
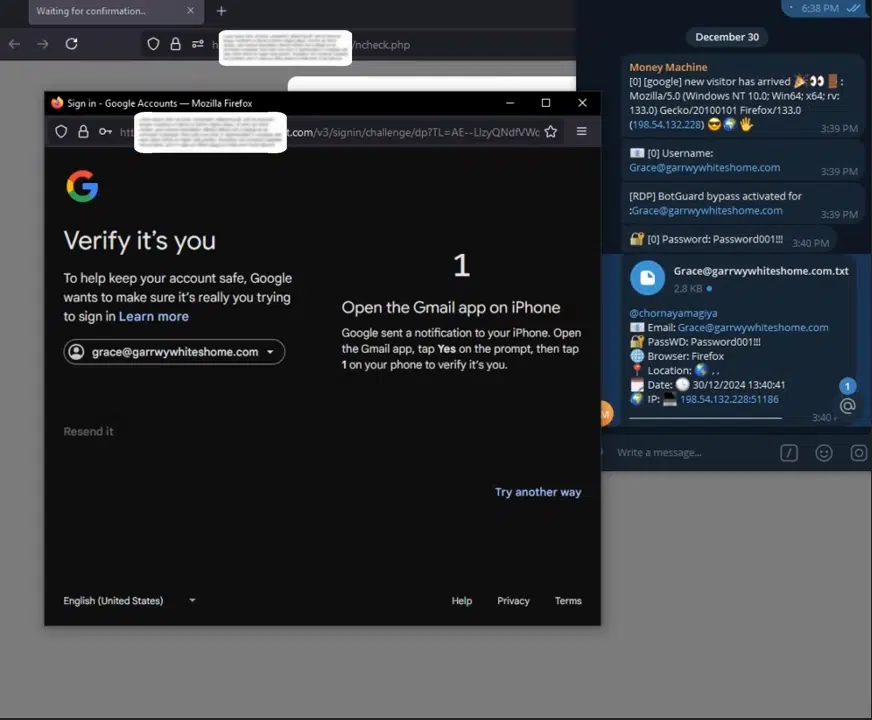
2. Attacker’s View: Live Credential Interception
Once the victim enters their credentials, the phishing kit forwards them to the attacker's panel in real-time. The second image reveals how attackers receive notifications via Telegram, complete with username, password, browser details, and even IP address. According to SlashNext’s findings, this real-time credential capture method allows cybercriminals to bypass 2FA almost instantly, making it particularly dangerous.
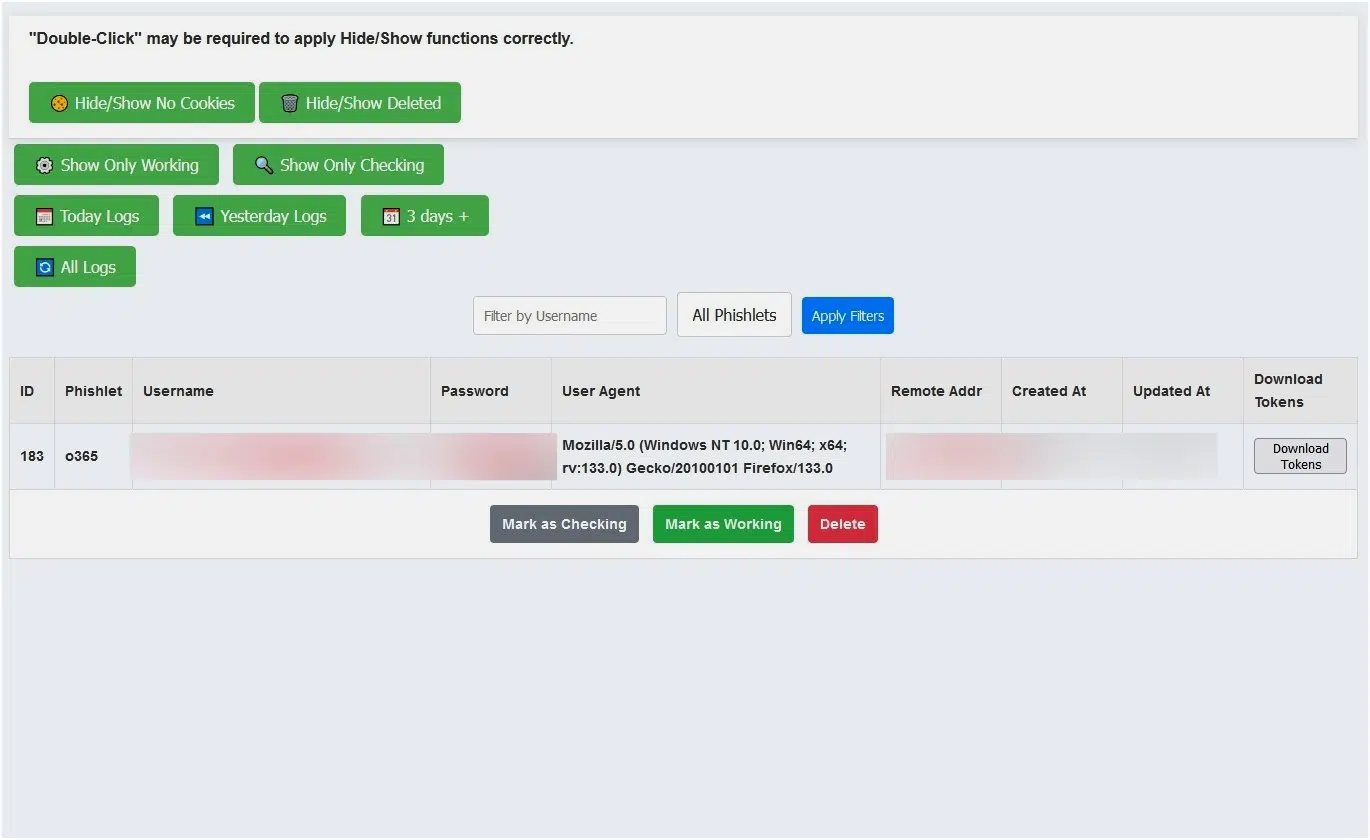
3. The Attack Panel: Stolen Credentials and Session Tokens
The third image provides an inside look at an attacker's web panel, where stolen login details are stored. The “Download Tokens” option seen in the interface highlights how attackers can bypass 2FA by using these stolen session tokens, preventing users from noticing any unauthorized access until it’s too late.
Why This Attack is Dangerous
- Bypasses 2FA Security: Since Astaroth captures session tokens, even users with authentication apps or SMS-based 2FA are at risk.
- Targets Personal & Business Accounts: With a focus on O365 and major email providers, this attack threatens both individuals and organizations.
- Automated & Scalable: Attackers can efficiently log, filter, and manage stolen credentials, making large-scale phishing campaigns more effective.
How to Protect Yourself
Cybersecurity experts advise users and organizations to take the following precautions:
- Verify URLs Before Logging In – Always check the web address before entering credentials. Phishing pages often use domains that look similar to official websites.
- Use Hardware Security Keys – Devices like YubiKey, which use FIDO2/WebAuthn authentication, make phishing nearly impossible.
- Monitor for Unauthorized Logins – Enable alerts for suspicious sign-ins and regularly check account activity.
- Avoid Clicking Unverified Links – If you receive an email prompting you to log in, visit the official website manually instead of clicking the link.
- Educate & Train Employees – Businesses should conduct regular phishing awareness training to help staff recognize threats.
According to SlashNext researchers, the Astaroth phishing kit represents a growing trend in cybercrime where attackers develop more sophisticated ways to compromise user security. As phishing tactics evolve, staying informed and adopting stronger authentication measures is more crucial than ever.
Reference:
SlashNext: Astaroth – A New 2FA Phishing Kit